AD Integration
Active Directory Connector
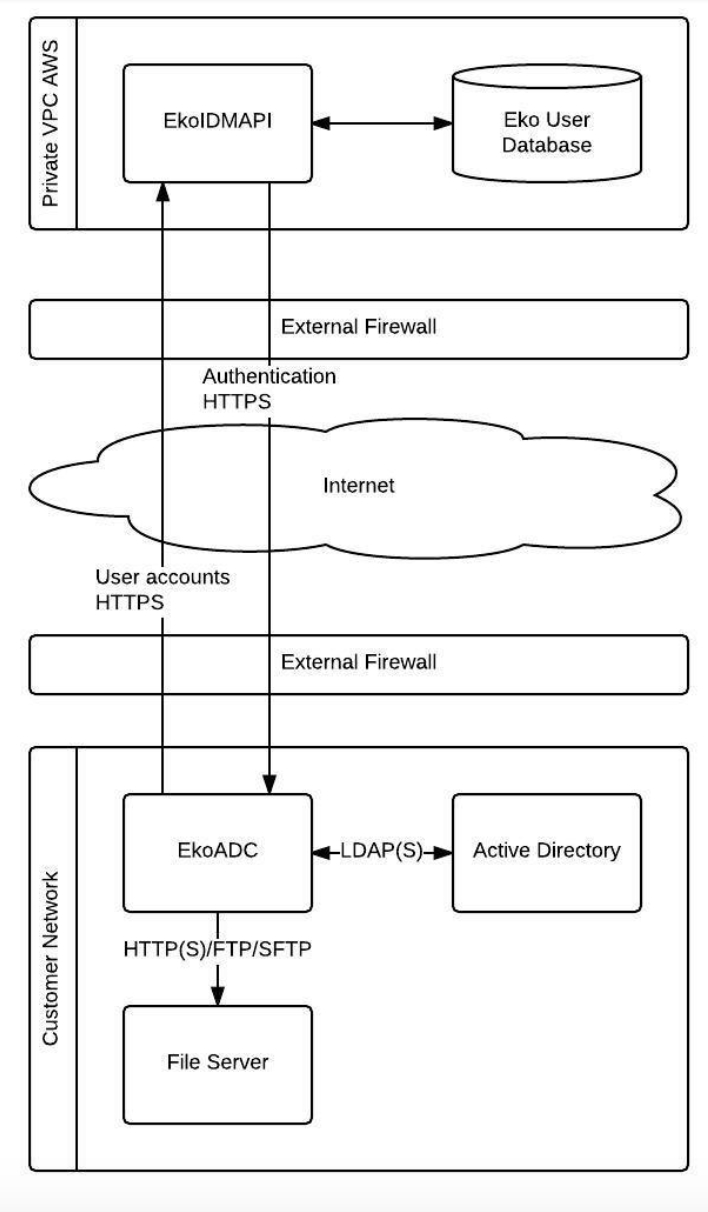
Eko’s active directory connector (EkoADC) is Eko’s proprietary software used for user synchronization and authentication which works with Microsoft Active Directory or other LDAP compatible identity management systems. EkoADC runs on a secure hardened Ubuntu image that can be installed both on-premise or on the cloud.
EkoADC is mainly responsible for two main tasks; user synchronization and user authentication.
EkoADC User Synchronization
EkoADC can be configured to talk with user directory via Lightweight Directory Access Protocol (LDAP) to fetch user data from customer’s directory service such as Microsoft Active Directory so that all accounts in user directory can be used with Eko Application.
EkoADC also supports user synchronization from Comma Separated Value (CSV) file via FTP/SFTP in case user profiles are stored in another database. However, each line in CSV file must contain user account (user ID) that can be used for mapping user account and LDAP binding.
Note: User synchronization from file should be used for user profile synchronization only. Directory software that supports LDAP is still required for user authentication.
EkoADC User Authentication
When a user logs into Eko by entering user account, user account information is passed to EkoADC via HTTPS. Upon receiving user account, EkoADC will perform LDAP binding for authentication. If authenticated successfully, EkoADC send back result to EkoIDMAPI
EkoADC Server Specification
CPU: >=4 Cores Memory: >=4 GB Disk: >=100 GB Network: >= 1Gb Ethernet with NAT OS Support : Ubuntu 20.04 LTS
Virtual Machine and OS provide by Customer, The Application provided by Eko Communications
Access Control for EkoADC
Eko ADC supported to synchronize employee directly from Active Directory or synchronize in CSV file format from customer’s file sharing (for this mode customer need to add AD’s user into the file for authentication purpose). Before start to install, customer need to pre-define the network access control as following
Source | Destination | Port |
EkoADC | Internet(Any) | TCP/443 |
Internet(Any) | EkoADC | TCP/443 |
EkoADC | Customer AD | LDAP, LDAPs |
EkoADC | Time server | NTP (TCP/123, UDP/123) |
EkoADC | DNS server | DNS (UDP/53) |
EkoADC | FTP server | TCP/FTP, TCP/FTPs |
Installation preparation
EkoADC component base on container services and the OS can running on both VM and Physical machine.
Customer need in pre-install the OS and software component as following
Ubuntu OS (We recommended to running on Ubuntu 20.04 LTS) and updated
with latest security patch/hotfix.
Docker CE (Installation Instruction: https://docs.docker.com/install/linux/docker-ce/ubuntu/)
Docker Compose utility (Installation instruction: https://docs.docker.com/compose/install/)
Installation instruction
EkoADC need to install on secure infrastructure and harden OS with latest security patch.
Login to Ubuntu OS with non root privilege
Create ./app with “mkdir app”
Go to the directory ./app and create file docker-compose.yaml, .env, config.json and copy starting configuration to the files.
Pull EkoADC Container with wget command:
Load docker container to docker engine with docker command:
Start the EkoADC container with docker-compose command
EkoADC will starting and you can access to the EkoADC web console from server ip with https protocol. That’s finished to install the EkoADC
The starting configurations include:
docker-compose.yaml
.env
config.json
Upgrade instruction
Pull the latest version of EkoADC Container with wget command:
Load docker container to docker engine with docker command:
Update file “.env” file with latest version of EkoADC
Start the EkoADC container with docker-compose command
Login to Web Console to update the configuration
Last updated